Cloud Security Best Practices for Secure Enterprise Growth

The growing adoption of cloud computing in enterprises has changed the way businesses operate and scale. But it has posed security threats like data breaches, malware attacks, misconfigurations, and more. Even a minor flaw in a shared cloud environment can do a lot of damage, sometimes bringing down whole systems. As organizations expand their cloud services, it is important to follow cloud security best practices.
In 2025, the cloud section of the global cybersecurity industry was worth 67.7%. This is because organizations are investing in cloud security solutions that work with both hybrid and multi-cloud systems. This also provides them with a single view, threat identification, and real-time response. This upholds that everyone uses the cloud safely, stays compliant, and keeps their operations running smoothly. Enterprise cloud security is very important since it protects data, apps and systems, and workloads on a large scale.
In this blog, we will guide you through cloud security best practices, enabling businesses to implement them by overcoming the challenges.
Table of Contents
Cloud Security Best Practices for Enterprises
There are a lot of cloud security challenges for large organizations, like access management, data exposure, visibility issues, etc. To deal with these challenges, you need organized and scalable cloud security best practices that make sure security measures work with your business’s cloud infrastructures.
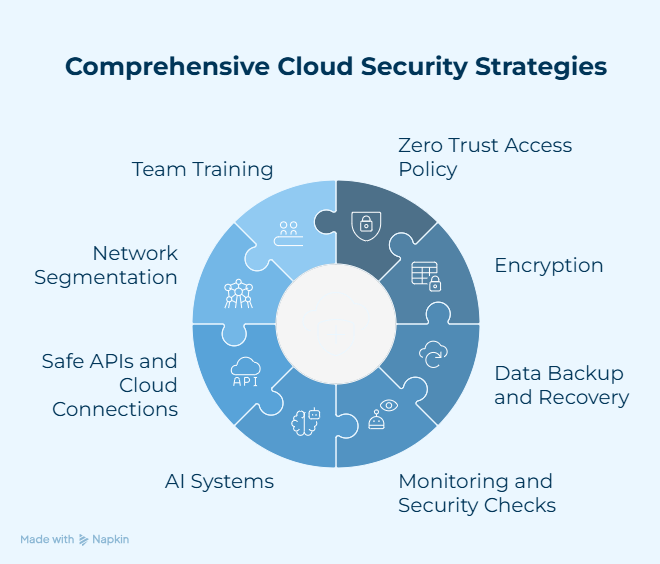
1. Use a Zero Trust Access Policy
Challenge: Big enterprises often have trouble with accounts that have too many permissions and access controls that don’t work the same way on all cloud platforms.
Best Practice: One of the most important cloud security best practices is to adopt Zero Trust, which means that no user or system is trusted automatically. Implementing least-privilege access, role-based restrictions, and multi-factor authentication ensures that someone will not get into your system without proper authorization. Identity monitoring and regular access evaluations make cloud security management for businesses stronger.
2. Use encryption on all levels of the cloud
Challenge: Storing data in more than one cloud environment increases the chances of breaches and regulatory issues.
Best Practice: End-to-end encryption of data keeps sensitive information safe while it’s being sent and stored. A unified key management system, automated key rotation, and consistent encryption standards make it easier for cloud risk management. This also makes sure that operations are safe and compliant in multi-cloud environments.
3. Improve your ability to back up and recover data
Challenge: If your backup plans and recovery plans are not good enough, you can lose all your data and miss out on valuable information.
Best Practice: Automated backups, geo-redundancy backups, and regular recovery testing are all important cloud security best practices. These measures are necessary when considering how to secure cloud infrastructure at scale because they ensure consistency.
4. Allow for ongoing monitoring and security checks
Challenge: Unclear visibility across cloud systems makes it harder to find risks and respond to them.
Best Practice: Regular audits, centralized logging systems, and constant monitoring are all important aspects of cloud security best practices. Using integrated cloud security solutions gives you real-time information, helps you find problems early, and proposes appropriate solutions.
5. Use AI systems to detect and respond to threats
Challenge: It is quite challenging to find AI-powered threats and complex attacks without superior systems since they change faster than traditional threats.
Best Practice: Using an AI-powered cloud security framework is a modern and relevant solution that makes it easier to find threats and deal with them automatically. This makes proactive cloud security strategies stronger, cuts down on the amount of work that needs to be done manually, and improves cloud systems at the enterprise level.
6. Safe APIs and Cloud Connections
Challenge: APIs make the attacked cloud region bigger, and they are often targeted because of inadequate security safeguards.
Best Practice: Strong authentication, constant monitoring, role-oriented access control, and regular testing are all important parts of cloud security best practices. These measures are very important for securing multi-cloud environments and making sure that API communications are safe.
7. Use network segmentation and encrypt traffic
Challenge: Attackers can move in a linear direction once they find a clear and flat network.
Best Practice: This is why segmenting the network and encrypting internal traffic becomes one of the important cloud security best practices. Such procedures keep workloads separate, minimize the chances and number of attacks, and ensure effective cloud risk management.
8. Train teams how to use the cloud safely
Challenge: Human error is very common, and sadly, bad settings are still the main sources of cloud security problems.
Best Practice: Ongoing training for workers and handing out a definite set of rules on how to run the business are two of the commendable cloud security best practices. Teams that are well-trained follow secure configuration standards, use cloud resources substantially, and complete the enterprise cloud security checklist.
By following these cloud security best practices, businesses can mitigate the chances of threats and keep their cloud environments secure. These best cloud security strategies for enterprises ensure that their assets are protected, meet the rules, and properly function in cloud environments.
Secure your cloud environment today by partnering with experts offering Azure Cloud Services that help enterprises implement security best practices at scale.
Future-Proof Your Cloud Security
How can Bloom help in implementing cloud security best practices?
To keep cloud environments safe, you need to know about the operations across departments, have a plan, and use sophisticated technologies. Bloom helps businesses use cloud security best practices to keep their data safe, stay compliant, and make their cloud platforms more resilient.
- Check and improve the security of the cloud: Bloom checks your cloud infrastructure for weaknesses, misconfigurations, and areas that are not conforming to the rules. This assessment lays the foundation for initiating cloud security best practices that are required for your business.
- Set up advanced security controls for Azure: Bloom uses Azure-native cloud security tools to enforce role-based access, encrypt data, administer APIs securely, and split up networks. These cloud security best practices keep workloads safe from attacks while making cloud security administration more efficient.
- Uses AI and automation to find threats: Bloom uses Azure AI-powered security tools to automate threat identification, scanning potential threats, and responding to attacks in real-time. This upgrades cloud services and improves response times in all enterprise cloud environments.
- Complies with Industry Standards: Bloom assists companies in upholding industry standards and putting cloud risk management plans into action by utilizing Azure compliance frameworks and governance tools. As a result, operational and regulatory risks are reduced.
- Constant Observation and Round-the-Clock Assistance: Bloom offers 24/7 assistance monitoring for Azure environments. This promises all-time availability, quick resolution of incidents, and continuous adherence to the cloud security best practices.
Conclusion
Cloud security is a holistic process that is constantly introducing new upgrades. As enterprises scale their operations, cloud security becomes a defense mechanism. Using cloud security best practices promises better visibility, improved governance, and immediate mitigation of threats across workloads. These practices help businesses grow and come up with innovative endeavors while protecting sensitive data. By implementing these practices, businesses can stay relevant and deal with emergencies confidently.
Another important point to keep in mind is that cloud security best practices do not depend only on the cloud provider. They function well when companies have a solid understanding of their own operations, risk considerations, and usage.
Ready to make cloud security an enabler for your business? Get in touch with us to put cloud security strategies into practice and improve business outcomes.
Frequently Asked Questions
Q1. What is enterprise cloud security?
Enterprise cloud security is the fixed set of rules, processes, technologies, and controls that businesses use to protect their cloud environments. It is mostly about keeping user access, workloads, cloud-based systems, and business data safe. By following cloud security best practices, businesses can get rid of risks, ensure they are following the rules, and keep their operations safe.
Q2. What is the difference between SaaS and enterprise cloud security?
The application security and the infrastructure are handled by the cloud provider in SaaS environments. Customers are still in charge of protecting their data, user access, workloads, etc., in SaaS environments. But enterprise cloud security employs definite cloud security best practices to provide an all-encompassing security measure throughout the entire cloud ecosystem. This extends the capabilities of individual SaaS solutions.
Q3. What is enterprise cloud computing?
A model that enables businesses to access cloud service providers’ computer resources, like storage, servers, apps, etc., is enterprise cloud computing. You only need to pay for the service you are taking. By this process, businesses improve their IT infrastructure, lower expenses, and expand operations.
Q4. What is cloud security?
The process of saving cloud-based systems, data, and services against unauthorized access and cyber threats is called cloud security. To protect cloud infrastructure and workloads, it employs advanced technology, governance guidelines, and access controls.
Q5. What is a cloud security strategy?
A cloud security strategy is an organized plan that ensures a company’s cloud assets are safe. It also includes privacy policies and role-based access. It sets up a set of rules, processes, and tools to keep data, systems, and infrastructure safe from cyber threats, misconfigurations, and other security risks.
Q6. How secure are cloud services?
The security of cloud services depends on many different factors. To have strong security, you need to use encryption, multi-factor authentication, restricted firewalls, endpoint protection, and continuous observation. To protect against emerging threats, you need to regularly update your software, address flaws, and follow cloud security best practices.
Q7. What makes a successful could-native security strategy?
An ideal cloud-native security plan takes into account the special features of cloud-native architectures, like containers, workflows, etc., that change with time. The first step in making strategies work is to make small, easy-to-implement security improvements to development processes, infrastructure, and operational workflows. By combining automation, real-time checks, and cloud security solutions, you can make sure that cloud security best practices are always followed.
Q8. What is a cloud compliance framework?
A cloud compliance framework is responsible for making sure that organizations abide by the legal terms and conditions and follow certain regulations. It lays out the rules, processes, and controls that must be in place to handle sensitive data. It ensures that organizations must follow rules like HIPAA, PCI DSS, and GDPR. With this, businesses can lower their regulatory risk, stay accountable, and make sure their cloud operations are safe.
Q9. What are cloud security standards?
Cloud security standards are definite rules that tell you how to best protect your cloud data, apps, and infrastructure. They focus on things like encryption, managing identities, access, and risks, and making sure they follow the rules. Standards like ISO/IEC and NIST help organizations manage security risks in a consistent way. Regulations like GDPR help organizations protect people’s privacy and establish trust between alliances.
Q10. What is cloud risk management?
Cloud risk management is the process by which businesses find, evaluate, and reduce security risks in complicated cloud settings, such as multi-cloud and hybrid settings. It helps security teams make smart choices by helping them understand the level of each risk, like how it could affect the business, and the like. Businesses can use cloud risk management to make the best use of their resources, eliminate risk, and keep their cloud environment safe.
Recent Posts
- When Should Businesses Bring in Azure Cloud Experts for Their Projects?
- Azure Cost Optimization: How Businesses Reduce Cloud Spend After Migration
- How Expert Cloud Consultants Manage Risk in Large-Scale Cloud Initiatives?
- Why You Need to Hire an Azure Cloud Engineer in 2026?
- When Should Businesses Hire DevOps Engineers for Cloud-Scale Delivery?
















